The task of data link layer is to convert the raw bit stream offered by the physical layer into a stream of frames for use by the network layer. Various framing methods are used , including character count, character stuffing, and bit stuffing. Data link protocols can provide error control to retransmit damaged or lost frames. To prevent a fast sender from overrunning a slower receiver, the data link protocol can also provide flow control. The sliding window mechanism is widely used to integrate error control and flow control in a convenient way.
Sliding window protocols can be categorized by the size of the sender's window and the size of the receiver's window. When both are equal to 1, the protocol is stop-and -wait. When the sender's window is greater than 1, for example to prevent the sender from blocking on a circuit with a long propagation delay, the receiver can be programmed either to discard all frames other than the next one in sequence (protocol 5) or buffer out of order frames until they are needed (protocol 6).
Protocols can be modeled using various techniques to help demonstrate their correctness. Finite state machine models and Petri net models are commonly used for this purpose.
Many networks use one of the bit-oriented protocols-SDLC, HDLC, ADCCP, or LAPB at the data link level. All of these protocols use flag types to delimit frames, and bit stuffing to prevent flag bytes from occurring in the data. All of them also use a sliding window for flow control. The Internet uses SLIP and PPP as data link protocols. ATM systems have their own simple protocol, which does a bare minimum of error checking and no flow control.
Friday, July 31, 2009
Quick Tech Lesson: Overview Of The Data Link Layer
Posted by
Sunflower
at
7/31/2009 11:35:00 AM
0
comments
![]()
Labels: Data Link layer, Error correction, Frames, Protocols
|
| Subscribe by Email |
|
Quick Tech Lesson: Overview Of The Physical Layer
The physical layer is the basis of all the networks. Nature imposes two fundamental limits on all channels, and these determine their bandwidth. These limits are the Nyquist limit, which deals with noiseless channels, and the Shammon limit, for noisy channels.
Transmission media can be guided or unguided. The principle guided media are twisted pair, coaxial cable, and fiber optics. Unguided media include radio, microwaves, infrared, and lasers through the air.
A key element in most wide area networks is the telephone system. Its main components are the local loops, trunks and switches. Local loops are analog-twisted pair circuits, which require modems for transmitting digital data. Trunks are digital, and can be multiplexed in several ways, including FDM, TDM and WDM. The switches include crossbars, space divison switches, and time divison switches. Both circuit switching and packet switching are important.
The telephone system are now becoming digital from end to end and carrying both voice and data traffic over the same lines. Two variants of this new system, known as ISDN, are being introduced. Narrowband ISDN is a circuit switched digital system that is an incremental improvement over the current system. In contrast, broadband ISDN represents a paradigm shift, since it is based on cell switching ATM technology. Various kinds of ATM switches exist, including the knockout switch and the Batcher-banyan switch.
For mobile applications, the hard-wired telephone system is not suitable. Alternatives to the telephone system include cellular radio and communication satellites. Cellular radio is now widely used for portable telephones but will soon be common for data traffic as well. The current generation of cellular systems (e.g. AMPS) are analog, but the next generation (e.g. PCS/PCN) will be fully digital. Transmission communication satellites are geosynchronous, and there was some interest in bigger systems, but the failure of Iridium slowed down this process.
Posted by
Sunflower
at
7/31/2009 11:03:00 AM
0
comments
![]()
Labels: Cellular radio, Computer networks, Networks, Telephone system, The Physical Layer, Transmission media
|
| Subscribe by Email |
|
Quick Tech Tip: Overview Of The Network Layer
The network layer provides services to the transport layer through virtual circuits or datagrams. In both cases, its main job is routing packets from the source to the destination. In virtual circuit subnets, a routing decision is made when the virtual circuit is set up. In datagram subnets, it is made on every packet.
Many routing algorithms are used in computer networks. Static algorithms include shortest path routing, flooding, and flow-based routing. Dynamic algorithms include distance vector routing and link state routing. Most actual networks use one of these. Other important routing techniques are hierarchical routing, routing for mobile hosts, broadcast routing, and multicast routing.
Subnets can become congested, increasing the delay and lowering the throughput for packets. Techniques include traffic shaping, flow specifications, and bandwidth reservation. If congestion does occur, it must be dealt with. Choke packets can be sent back, load can be shed, and other methods applied.
Networks differ in various ways, so when multiple networks are connected together problems can occur. Sometimes problems can be finessed by tunneling a packet through a hostile network, but if the source and the destination networks are different, this approach fails. Fragmentation may be called for if different networks are having different maximum sizes.
The Internet has a rich variety of protocols related to the network layer. These include the data protocol, IP, but also the control protocols ICMP, ARP, and RARP, and the routing protocols OSPF and BGP. The Internet is rapidly running out of IP addresses, so a new version of IP, IPv6, has been developed.
Unlike the datagram-based Internet, ATM networks use virtual circuits inside. There must be a set up before data can be transferred and torn down after transmission is completed. Quality of service and congestion control are major issues with ATM networks.
Posted by
Sunflower
at
7/31/2009 10:43:00 AM
0
comments
![]()
Labels: Concatenated Virtual Circuits, Congestion, Datagrams, Network layer, Networks, Packets, Technical Tip
|
| Subscribe by Email |
|
Thursday, July 30, 2009
Quick Tech Tip: CDMA - Code Division Multiple Access
CDMA (Code-Division Multiple Access) refers to any of several protocols used in so-called second-generation (2G) and third-generation (3G) wireless communications. As the term implies, CDMA is a form of multiplexing, which allows numerous signals to occupy a single transmission channel, optimizing the use of available bandwidth. CDMA, a proprietary standard designed by Qualcomm in the United States, has been the dominant network standard for North America and parts of Asia.
Coverage: The most important factor is getting service in the areas you will be using your phone. Upon viewing competitors' coverage maps you may discover that CDMA carriers offer cellular service in your area. If so, there is no decision to be made, but most people will find that they do have a choice.
For radio systems there are two resources, frequency and time. Division by frequency, so that each pair of communicators is allocated part of the spectrum for all of the time, results in Frequency Division Multiple Access (FDMA). Division by time, so that each pair of communicators is allocated all (or at least a large part) of the spectrum for part of the time results in Time Division Multiple Access (TDMA). In Code Division Multiple Access (CDMA), every communicator will be allocated the entire spectrum all of the time. CDMA uses codes to identify connections.
CDMA is a form of spread-spectrum, a family of digital communication techniques that
have been used in military applications for many years. The core principle of spread
spectrum is the use of noise-like carrier waves, and, as the name implies, bandwidths
much wider than that required for simple point-to-point communication at the same data rate. CDMA is a Direct Sequence Spread Spectrum system. The CDMA system works directly on 64 kbit/sec digital signals. These signals can be digitized voice, ISDN channels, modem data, etc.
CDMA is altering the face of cellular and PCS communication by:
· Dramatically improving the telephone traffic capacity.
· Dramatically improving the voice quality and eliminating the audible effects of
multipath fading.
· Reducing the incidence of dropped calls due to handoff failures.
· Providing reliable transport mechanism for data communications, such as
facsimile and internet traffic.
· Reducing the number of sites needed to support any given amount of traffic.
· Simplifying site selection.
· Reducing deployment and operating costs because fewer cell sites are needed.
· Reducing average transmitted power.
· Reducing interference to other electronic devices.
· Reducing potential health risks.
Posted by
Sunflower
at
7/30/2009 06:10:00 PM
0
comments
![]()
Labels: CDMA, Code Divison Multiple Access, digital, Multilexing, Spread spectrum, Technical Tip
|
| Subscribe by Email |
|
Wednesday, July 29, 2009
Quick Tech Tip: Encapsulation - What does it mean ?
Encapsulation is not a common word in the English language; however, it is an important phrase in the word of software design, especially in the world of Object Oriented Programming. So what does encapsulation mean ?
In computer science, the principle of information hiding means the hiding of design decisions in a computer program, those decisions that are most likely to change, thus protecting other parts of the program from change; especially if the design decision is changed. The protection involves providing a stable interface which shields the remainder of the program from the implementation (the details that are most likely to change). The purpose is to achieve potential for change: the internal mechanisms of the component can be improved without impact on other components, or the component can be replaced with a different one that supports the same public interface.
The term encapsulation is often used interchangeably with information hiding, while some make distinctions between these two terms (although to most people these terms seem the same). It seems that people, however, fail to agree on the distinctions between information hiding and encapsulation though one can think of information hiding as being the principle and encapsulation being the technique. A software module hides information by encapsulating the information into a module or other construct which presents an interface.
The concept of encapsulation is a term that is an integral part of object-oriented programming, where the interface to an object is defined by its public methods, while its internal state is represented by private data. Encapsulation is a good principle of object oriented design, and part of well designed systems.
Posted by
Ashish Agarwal
at
7/29/2009 11:03:00 PM
0
comments
![]()
Labels: Definition, Design, Object Oriented, Software
|
| Subscribe by Email |
|
Friday, July 24, 2009
Quick Tech Tip: Types Of Firewalls
There are several classifications of firewalls depending on where the communication is taking place, where the communication is intercepted and the state that is being traced.
1. Packet Filtering Firewall : A packet filtering firewall will examine the information contained in the header of a packet of information which, is attempting to pass through the proverbial 'drawbridge into the castle'. It works on the network level of the OSI. This type of firewall only examines the header information. If data with malicious intent is sent from a trusted source, this type of firewall is no protection. When a packet passes the filtering process, it is passed on to the destination address. If the packet does not pass, it is simply dropped. This model is the best known and most widely used model for describing networking environments."
2. Stateful Packet Inspection : They filter packets at the network level and they recognize and process application-level data, but since they don't employ proxies, they deliver reasonably good performance in spite of the deep packet analysis. On the downside, they are not cheap, and they can be difficult to configure and administer.
3. Application Level Proxy : The slowest and most unwieldy firewall is the application level proxy. This type of firewall works on the application level of the protocol stack, which enables it to perform with more intelligence than a packet filtering or circuit gateway firewall.hey determine if a connection to a requested specific application is permitted such as, Internet access or Email. This allows the user to determine what application their computers will be used for. Also known as proxy servers they not only screen packets and determine what applications are permitted to be accessed but also offer protection from outside sources by hiding internal computers from external viewing.
4. Circuit Gateways : Circuit gateway firewalls work on the transport level of the protocol stack. They are fast and transparent, but really provide no protection from attacks. Circuit gateway firewalls also do not check the data in the packet. The one great benefit to this type of firewall is that they make the LAN behind the firewall invisible, as everything coming from within the firewall appears to have originated from the firewall itself. This is the least used type of firewall.
5. Network-Level Firewalls : The first generation of firewalls (c. 1988) worked at the network level by inspecting packet headers and filtering traffic based on the IP address of the source and the destination, the port and the service. Network-level firewalls are fast, they do not support sophisticated rule-based models. They don’t understand languages like HTML and XML, and they are capable of decoding SSL-encrypted packets to examine their content. As a result, they can’t validate user inputs or detect maliciously modified parameters in an URL request. This leaves your network vulnerable to a number of serious threats.
6. Internet Connection Firewall : Windows XP provides Internet security in the form of the new Internet Connection Firewall (ICF). ICF makes use of active packet filtering, which means the ports on the firewall are opened for as long as needed to enable you to access the services you are interested in.
Introduction to Firewalls
A firewall is a hardware or software system that prevents unauthorized access to or from a network. They can be implemented in both hardware and software, or a combination of both. Firewalls are frequently used to prevent unauthorized Internet users from accessing private networks connected to the Internet. All data entering or leaving the Intranet pass through the firewall, which examines each packet and blocks those that do not meet the specified security criteria.
Firewalls can greatly enhance the security of a host or a network. They can be used to do one or more of the following things:
* To protect and insulate the applications, services and machines of your internal network from unwanted traffic coming in from the public Internet.
* To limit or disable access from hosts of the internal network to services of the public Internet.
* To support network address translation (NAT), which allows your internal network to use private IP addresses and share a single connection to the public Internet (either with a single IP address or by a shared pool of automatically assigned public addresses).
FIREWALL CONCEPTS
There are two basic ways to create firewall rulesets: “inclusive” or “exclusive”. An exclusive firewall allows all traffic through except for the traffic matching the ruleset. An inclusive firewall offers much better control of the outgoing traffic, making it a better choice for systems that offer services to the public Internet. It also controls the type of traffic originating from the public Internet that can gain access to your private network. All traffic that does not match the rules, is blocked and logged by design.
Inclusive firewalls are generally safer than exclusive firewalls because they significantly reduce the risk of allowing unwanted traffic to pass through them.
HOW FIREWALLS WORK ?
A firewall, working closely with a router program, examines each network packet to determine whether to forward it toward its destination. A firewall also includes or works with a proxy server that makes network requests on behalf of workstation users. A firewall is often installed in a specially designated computer separate from the rest of the network so that no incoming request can get directly at private network resources.
Firewalls use one or more of three methods to control traffic flowing in and out of the network:
* Packet filtering - Packets are analyzed against a set of filters. Packets that make it through the filters are sent to the requesting system and all others are discarded.
* Proxy service - Information from the Internet is retrieved by the firewall and then sent to the requesting system and vice versa.
* Stateful inspection - It compares certain key parts of the packet to a database of trusted information. Information traveling from inside the firewall to the outside is monitored for specific defining characteristics, then incoming information is compared to these characteristics. If the comparison yields a reasonable match, the information is allowed through. Otherwise it is discarded.
Posted by
Sunflower
at
7/24/2009 10:34:00 AM
0
comments
![]()
Labels: Concepts, Firewalls, How does firewall work, introduction, Network layer, w
|
| Subscribe by Email |
|
Introduction to Packet Fragmentation
Each network imposes some maximum size on its packets. The network designers are not free to choose any maximum packet size they wish as there are various factors like hardware, operating system, protocols, compliance with some (inter)national standard, desire to reduce error induced transmissions to some level and desire to prevent one packet from occupying the channel too long.
Packets larger than the allowable MTU (Maximum Transmission Unit) must be divided into multiple smaller packets, or fragments, to enable them to traverse the network.
If a packet that is about to be sent (for eg : over an Ethernet link) is bigger than that, the router which is about to send the packet over that link will fragment the packet i.e. the router will split the packet up into smaller messages (known as fragments) that are each small enough to be transmitted over the link. When the fragments arrive at their destination (the computer to which they are being sent), that computer can reassemble the fragments to recover the original message - assuming none of the messages are lost in transit.
How can be fragmentation avoided ?
If the option of "don't fragment" is set ON in IP version 4, and the router wants to send the packet over a link for which the packet is too large, the router will not send the packet at all. Instead, the router will send a message back to the sender of the packet that was too large. The sending computer can then respond to this by sending out smaller packets. This is known as "path MTU discovery".
Strategies for recombining fragments :
- Transparent Fragmentation : When an oversized packet arrives at gateway, the gateway breaks it into smaller fragments, each fragment is addressed to same exit gateway, where pieces are recombined. In this way passage through the small packet network has been made transparent.
Benefits : It maximizes bandwidth on higher links and deterministic fragmentation unlikely.
Drawbacks : Packets may be reassembled/fragmented, gateways more complex, performance gains bounded because the max TU will be the MTU of the first hop. Plus, the IP layer at the destination may still have to perform reassembly if the last link had a smaller MTU than the first link. Only use on links with unusually small MTUs. 
- Non transparent Fragmentation : This strategy includes refraining the recombining of fragmented packets at intermediate gateway. Once a packet is fragmented, each fragment is treated as an original packet. All fragments are passed through the exit gateway. Recombination exists only at destination host.
Benefits : Multiple exit gateways can now be used and higher performance can be achieved.
Drawbacks : Overhead increases. Also, it requires every host to be able to do reassembly.
Posted by
Sunflower
at
7/24/2009 09:35:00 AM
0
comments
![]()
Labels: Fragmentation, Network layer, Networks, Non Transparent fragmentation, Packet fragmentation, Transparent fragmentation
|
| Subscribe by Email |
|
Wednesday, July 22, 2009
Quick Tech Tip: Layer 2 Tunneling protocol : L2TP
Layer Two Tunneling Protocol (L2TP) is an extension of the Point-to-Point Tunneling Protocol (PPTP) used by an Internet service provider (ISP) to enable the operation of a virtual private network (VPN) over the Internet.
The two end components that make up L2TP are the L2TP Access Concentrator (LAC) which is the device that physically terminates a call and the L2TP Network Server (LNS), which is the device that terminates and possibly authenticates the PPP stream. Once a tunnel is established, the network traffic between the peers is bidirectional. To be useful for networking, higher level protocols are then run through the L2TP tunnel. To facilitate this L2TP session (or call) is established within the tunnel for each higher-level protocol such as PPP. Either the LAC or LNS may initiate sessions. The traffic for each session is isolated by L2TP, so it is possible to set up multiple virtual networks across a single tunnel.
The packets exchanged within an L2TP tunnel are either categorized as control
packets or data packets. L2TP provides reliability features for the control packets, but no reliability for data packets. Reliability, if desired, must be provided by the nested protocols running within each session of the L2TP tunnel.
An L2TP tunnel can extend across an entire PPP session or only across one segment of a two-segment session. This can be represented by four different tunneling models :
- Voluntary Tunnel model : a tunnel is created by the user, typically by the use of an L2TP enabled client which is called the LAC client. The user will send L2TP packets to the Internet Service Provider (ISP) which will forward them on to the LNS.
- Compulsory tunnel model-incoming call: a tunnel is created between ISP LAC and the LNS home gateway.
- Compulsory tunnel model-remote dial the home gateway (LNS) initiates a tunnel to an ISP (LAC) (outgoing call) and instructs the ISP to place a local call to the PPP enabled client which is the remote user.
- L2TP Multi-hop connection : It is a way of redirecting L2TP traffic on behalf of client LACs and LNSs. A Multi-hop connection is established using an L2TP Multi-hop gateway. A tunnel is established from a client LAC to the L2TP Multi-hop gateway and then another tunnel is established between the L2TP Multi-hop gateway and a target LNS. L2TP traffic between client LAC and LNS is redirected to each other through the gateway.
Posted by
Sunflower
at
7/22/2009 10:51:00 AM
0
comments
![]()
Labels: L2TP, Layer Two Tunneling Protocol (L2TP), Network, Point-to-point protocol, PPP, traffic, virtual private network, VPN
|
| Subscribe by Email |
|
Quick Tech Tip: Point-to-point tunneling protocol - PPTP
Overview of Point-to-point Protocol:
The Point-to-Point Protocol (PPP) provides a standard method for transporting multi-protocol datagrams over point-to-point links. PPP was originally emerged as an encapsulation protocol for transporting IP traffic between two peers.PPP is comprised of the following main components:
* Encapsulation: A method for encapsulating multi-protocol datagrams.
* Link Control Protocol: The LCP is used to automatically agree upon the encapsulation format options, handle varying limits on sizes of packets, detect a looped-back link and other common misconfiguration errors, and terminate the link.
* Network Control Protocol: An extensible Link Control Protocol (LCP) for establishing, configuring, and testing and managing the data-link connections.
* Configuration: Easy and self configuration mechanisms using Link Control Protocol. This mechanism is also used by other control protocols such as Network Control Protocols (NCPs).
Introduction TO PPTP :
PPTP packages data within PPP packets, then encapsulates the PPP packets within IP packets (datagrams) for transmission through an Internet-based VPN tunnel. PPTP supports data encryption and compression of these packets.
The PPTP protocol is designed to perform the following tasks:
* Query the status of Comm Servers
* Provide In-Band management
* Allocate channels and place outgoing calls
* Notify NT Server on incoming calls
* Transmit and Receive User Data with flow control in both directions
* Notify NT Server on disconnected calls.
PPTP-based Internet remote access VPNs are by far the most common form of PPTP VPN. In this environment, VPN tunnels are created via the following two-step process:
1. The PPTP client connects to their ISP using PPP dial-up networking.
2. Via the broker device (described earlier), PPTP creates a TCP control connection between the VPN client and VPN server to establish a tunnel.
Once the VPN tunnel is established, PPTP supports two types of information flow:
* control messages for managing and eventually tearing down the VPN connection. Control messages pass directly between VPN client and server.
* data packets that pass through the tunnel, to or from the VPN client.
PPTP also supports VPN connectivity via a LAN.
PPTP supports authentication, encryption, and packet filtering.
Though PPTP remains a popular choice for VPNs, one drawback of PPTP is its failure to choose a single standard for authentication and encryption. Two products that both fully comply with the PPTP specification may be totally incompatible with each other if they encrypt data differently.
Posted by
Sunflower
at
7/22/2009 10:25:00 AM
0
comments
![]()
Labels: Network, Point-to-point protocol, Point-to-point tunneling protocol, PPP, PPTP, Technical Tip, Tunneling, virtual private network, VPN
|
| Subscribe by Email |
|
Quick Technical Tip : Tunneling
Tunneling is a way in which data is transferred between two networks securely. All the data that is being transferred are fragmented into smaller packets or frames and then passed through the tunnel. This process is different from a normal data transfer between nodes. Every frame passing through the tunnel will be encrypted with an additional layer of tunneling encryption and encapsulation which is also used for routing the packets to the right direction. This encapsulation would then be reverted at the destination with decryption of data which is later sent to the desired destined node.
Example: People have written tunnels over ICMP, DNS, HTTP, e-mail messages, and TCP connections. Tunnels can either by of the "port redirector" style (which run on top of any TCP/IP stack) or of the network interface variety (below the TCP/IP stack requiring kernel mod).
VPN connection are of two type, PPTP (Point-to-Point tunneling protocol) and L2TP (Layer 2 tunneling protocol). Both PPTP and L2TP tunnels are nothing but local sessions between two different endpoints. Incase they have to communicate then the tunneling type must be negotiated between the endpoint, either PPTP or L2TP and then more configurable parameters like encryption, address assignment, compression etc must be configured in order to get the best possible security over the internet based private logical tunnel communication. This communication is created, maintained and terminated using a tunnel management protocol.
Data can be sent once the tunnel is in place and clients or server can use the same tunnel to send and receive data across the internetwork. The data transfer depends upon the tunneling protocols being used for the transfer.
Posted by
Sunflower
at
7/22/2009 10:23:00 AM
0
comments
![]()
Labels: L2TP, Layer 2 tunneling protocol, Network, Networks, Point-to-point protocol, Protocols, Transfer of data
|
| Subscribe by Email |
|
Sunday, July 19, 2009
Quick Tech Tip - Connectionless Internetworking
Connectionless internetworking follows the datagram model. In this model, the network layer offers the transport layer the ability to inject datagrams into the subnet. There is no notion of a virtual circuit at all in the network layer. This model does not require all packets belonging to one connection to traverse the same sequence of gateways.
A routing decision is made separately for each packet, possibly depending on the traffic at the moment the packet is sent. This strategy can use multiple routes and thus achieve a higher bandwidth than the concatenated virtual circuit model.

Datagrams are constructed and sent in the usual way. Routing decisions are made on a packet by packet basis so that we cannot even guarantee that all the packets in a message will be sent over the same set of networks. Since each of the networks can have different properties the processing that the packets receive will be different depending on the route they took.
Since each network will have its own network layer protocol we cannot simply transfer network layer packets across the routers. One possibility is to try and convert from one protocol to another but this is not very successful for much the same set of reasons that converting between the different frame types of the 802 Ethernets was difficult.
A major issue in transferring from one network to another is that of addressing. In general different networks use different addressing schemes. One possibility would be to assign every host an address for every sort of network but apart from being inefficient (lots of addresses would never be used) it would also require a huge translation table to be kept.
What IP (Internet Protocol) attempts to do is to define a universal packet which can be carried across all networks. Of course others have also had this idea so there are several ‘universal’ schemes and these have to be dealt with as well.
A major advantage of the datagram approach is that it can be used over subnets that do not use virtual circuits inside. Many LANs, mobile networks and even some WANs fall into this category. When an internet includes one of these, serious problem occurs if the networking strategy is based on virtual circuits.
Posted by
Sunflower
at
7/19/2009 12:31:00 AM
0
comments
![]()
Labels: Connectionless, Connectionless Internetworking, Datagram model, Datagrams, Internetworking, Multiprotocol routers, Network, Technical Tip
|
| Subscribe by Email |
|
Thursday, July 16, 2009
Quick Tech Tip: Concatenated Virtual Circuits
Two styles of internetworking are common:
* a connection-oriented concatenation of virtual circuit subnets,
* a datagram internet style.
In the concatenated virtual circuit model, a connection to a host in a distant network is set up in a way similar to the way connections are normally established. The virtual circuit consists of concatenated virtual circuits between the routers or gateways along the way from the source node to the destination node. Each gateway maintains tables telling which virtual circuits pass through it, where they are to be routed, and what the new virtual circuit number is. This process continues until the destination host has been reached.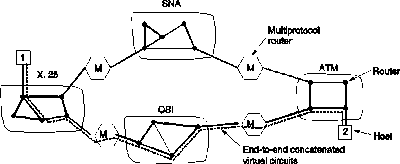
Once data packets begin flowing along the path, each gateway relays incoming packets, converting between packet formats and virtual circuit numbers as needed. Clearly, all data packets must traverse the same sequence of gateways , and thus arrive in order.
This scheme works best when all the networks have roughly the same properties.
Concatenated virtual circuits are also common in the transport layer. In particular, it is possible to build a bit pipe using OSI, which terminates in a gateway, and have a TCP connection go from the gateway to the next gateway. In this manner, an end-to-end virtual circuit can be built spanning different networks and protocols.
Posted by
Sunflower
at
7/16/2009 12:16:00 PM
0
comments
![]()
Labels: Concatenated Virtual Circuits, Gateways, Internetworking, Network layer, Packets, Routers
|
| Subscribe by Email |
|
Tuesday, July 14, 2009
Quick Tech Tip: InterNetworking
What are we talking about ? The interconnection of two or more networks, usually local area networks so that data can pass between hosts on the different networks as though they were one network. This requires some kind of router or gateway to facilitate the process of interconnecting two or more individual networks to facilitate communications among their respective nodes. Note: The interconnected networks may be different types. Each network is distinct, with its own addresses, internal protocols, access methods, and administration.
For different networks to interact, devices such as repeaters, bridges, routers, gateways are required. Repeaters are low level devices that just amplify or regenerate weak signals. They are needed to provide current to drive long cables. They copy individual bits between cable segments.
Unlike repeaters, bridges are store and forward devices. A bridge accepts the whole frame and passes it to the data link layer where the checksum is verified. Then the frame is sent down to the physical layer for forwarding on a different network.
Multiprotocol routers are conceptually similar to bridges, except that they are found in the network layer. They take incoming packets from one line to another, just as all routers do, but the lines may belong to different networks and use different protocols.
Transport gateways connect byte streams in the transport layer. Application gateways connects two parts of an application in the application layer.
When a gateway is between two WANs run by different organizations in different countries, the gateway is ripped apart in the middle and the two parts are connected with a wire.
Posted by
Sunflower
at
7/14/2009 12:40:00 PM
0
comments
![]()
Labels: Bridges, Gateways, Internetworking, Multiprotocol routers, Repeaters, Routers, Technical Tip
|
| Subscribe by Email |
|
Quick Tech Tip: Wireless Networks
The wireless communication revolution is bringing fundamental changes to data networking, telecommunication, and is making integrated networks a reality. By freeing the user from the cord, new systems (personal communications networks, wireless LAN's, mobile radio networks and cellular systems, etc), harbor the promise of fully distributed mobile computing and communications, in a new paradigm of any time, anywhere.
A wireless network allows you to connect your computer to a network using radio waves instead of wires. As long as you are within range of a wireless access point, you can move your computer from place to place while maintaining un-ethered access to networked resources. This can make networking extremely portable.
Wireless networks are of great value to fleets of trucks, taxis, buses and repair persons for keeping in contact with home. Another use is for rescue workers at disaster sites where the telephone system has been destroyed such as in the aftermath of Hurricane Katrina. Wireless networks are very important to the military.
Some wireless data networks run over wireless voice networks, such as mobile telephone networks (CPDP, HSCSD, PDC-P, and GPRS are examples). Other wireless networks run on their own physical layer networks, utilizing anything from antennas built into handlheld devices to large antennas mounted on towers. 802.11, LMDS, and MMDS are examples.
A few wireless networks are intended only to connect small devices over short distances. Bluetooth is an example.
Wireless LANs are networks are set up to provide wireless connectivity within a finite coverage area. Typical coverage areas might be a hospital (for patient care systems), a university, the airport, or a gas plant. They usually have a well-known audience in mind.
Wireless Personal Area Networking (WPAN) describes an application of wireless technology that is intended to address usage scenarios that are inherently personal in nature. The emphasis is on instant connectivity between devices that manage personal data or which facilitate data sharing between small groups of individuals.
Posted by
Sunflower
at
7/14/2009 11:25:00 AM
0
comments
![]()
Labels: Network, Personal Area Networking, Wireless, Wireless Local Area Networking, Wireless Networks, WLAN, WPAN
|
| Subscribe by Email |
|
Thursday, July 9, 2009
Quick Tech Tips: Wide Area Networks - WAN
Wide Area Networks, or WAN, span a large geographical area. A WAN contains a collection of machines intended for running user programs. Transmission rates are typically 2 Mbps, 34 Mbps, 45 Mbps, 155 Mbps, 625 Mbps, etc.
The machines are connected by a subnet whose job is to carry messages from machine to machine. The subnet consists of two distinct components : transmission lines and switching elements. Transmission lines move bits between machines. The switching elements are specialized computers used to connect two or more transmission lines. It is the job of the switching element to decide which outgoing line to choose to forward the data on incoming line.
In WANs, the network contains numerous cables or telephone lines, each one connecting a pair of routers. When a packet is sent from one router to another via one or more intermediate routers, the packet is received at each intermediate router in its entirety, stored there until the required output line is free, and then forwarded. A subnet using this principle is called a point-to-point, store and forward, or packet switched network.
Second option for a WAN is satellite or ground radio system. Each router has an antenna through which it can send and receive. All routers can hear the output from the satellite, and in some cases they can also hear the upward transmissions of their fellow routers to the satellite as well.
Posted by
Ashish Agarwal
at
7/09/2009 11:20:00 PM
0
comments
![]()
Labels: Network, Routers, subnet, transmission, WAN, Wide area network
|
| Subscribe by Email |
|
Quick Tech Tip : Metropolitan Area Networks - MANs
A metropolitan area network, or MAN is basically a bigger version of LAN. MAN is a computer networks usually spanning a campus or a city, which typically connect a few local area networks using high speed backbone technologies. A MAN supports both data and voice. A MAN just has one or two cables and does not contain switching elements.
A MAN is optimized for a larger geographical area than a LAN, ranging from several blocks of buildings to entire cities. MANs can also depend on communications channels of moderate-to-high data rates. A MAN might be owned and operated by a single organization, but it usually will be used by many individuals and organizations. MANs might also be owned and operated as public utilities. They will often provide means for internetworking of local networks. Metropolitan area networks can span up to 50km, with the devices being used such as modem and wire/cable devices.
The standard that has been adopted for MANs is called DQDB (Distributed Queue Dual Bus). DQDB consists of two unidirectional cables or buses to which all other computers are connected. Each bus has a head-end which initiates transmission activity.
There are three important features which discriminate MANs from LANs or WANs:
1. The network size falls intermediate between LANs and WANs. A MAN typically covers an area of between 5 and 50 km range. Many MANs cover an area the size of a city, although in some cases MANs may be as small as a group of buildings.
2. A MAN, its communications links and equipment are generally owned by either a consortium of users or by a network service provider who sells the service to the users.
3. A MAN often acts as a high speed network to allow sharing of regional resources. It is also frequently used to provide a shared connection to other networks using a link to a WAN.
Posted by
Ashish Agarwal
at
7/09/2009 10:55:00 PM
0
comments
![]()
Labels: LAN, Management, Metropolitan Area Network, Network, transmission
|
| Subscribe by Email |
|
Quick Tech Explanation: Local Area Networks - LANs
Local Area networks, generally called LANs, are privately owned networks within a single building or campus of up to a few kilometers in size. Most local area networks are built with relatively inexpensive hardware such as Ethernet cables, network adapters, and hubs. Wireless LAN and other more advanced LAN hardware options also exist as a part of modern LANs.
The most common type of local area network is an Ethernet LAN. If you look at size of LAN's, the smallest home LAN can have exactly two computers; a large LAN can accommodate many thousands of computers. Many of the larger LANs are divided into logical groups called subnets.
LANs are distinguished from other kinds of networks by three characteristics:
1. Size: LANs have a size limit and cannot expand beyond this size, essentially meaning that it is possible to plan and design for the worst case transmission time.
2. Topology: This is the geometric arrangement of devices on the network. For example, devices can be arranged in a ring or in a straight line. In a bus network, one machine is master and is allowed to transmit. An arbitration mechanism is needed to resolve conflicts when two or more machines want to transmit simultaneously.
In ring network, each bit propgates around on its own, not waiting for the rest of the packet to which it belongs.
3. Protocols: The rules and encoding specifications for sending data. The protocols also determine whether the network uses a peer-to-peer or client/server architecture.
4. Media: Devices can be connected by twisted-pair wire, coaxial cables, or fiber optic cables. Some networks do without connecting media altogether, communicating instead via radio waves.
Most LANs connect workstations and personal computers. Each node (individual computer) in a LAN has its own CPU with which it executes programs, but it also is able to access data and devices anywhere on the LAN. This means that many users can share expensive devices, such as laser printers, as well as data. Users can also use the LAN to communicate with each other, by sending e-mail or engaging in chat sessions.
LANs are capable of transmitting data at very fast rates, much faster than data can be transmitted over a telephone line; but the distances are limited, and there is also a limit on the number of computers that can be attached to a single LAN.
Posted by
Ashish Agarwal
at
7/09/2009 10:35:00 PM
0
comments
![]()
Labels: LAN, Local Area Network, Network, Technical Tip, Topology, transmission
|
| Subscribe by Email |
|
Tuesday, July 7, 2009
Quick Tech Tip - FDDI - Fiber distributed data interface
Fiber distributed data interface (FDDI) provides a standard for data transmission in a local area network that can extend in range up to 200 kilometers (124 miles). FDDI is a token-passing, fiber ring, network. The fiber optic media can be multimode fiber and can be as large as 100 kilometers - with no more than 2 kilometers between nodes.
Why FDDI?
- More Powerful Workstations and Servers.
- Resource Intensive Network Applications.
- Growing Distributed Client/Server Applications.
- Larger Spans of Distributed Networks.
- Increasing Numbers of Network Users.
- Bigger and More Powerful Software Applications.
FDDI Benefits:
- Higher Capacity and Performance than older LANs.
- More Simultaneous Transactions.
- Higher Availability (dual ring topology).
- Predetermined Performance (adding users have minimal impact on throughput).
- Longer Distance Loops (2 kilometers to 100 kilometer).
FDDI uses dual-ring architecture with traffic on each ring flowing in opposite directions (called counter-rotating). The dual rings consist of a primary and a secondary ring. During normal operation, the primary ring is used for data transmission, and the secondary ring remains idle.
FDDI specifies the physical and media-access portions of the OSI reference model. FDDI is not actually a single specification, but it is a collection of four separate specifications, each with a specific function. Combined, these specifications have the capability to provide high-speed connectivity between upper-layer protocols such as TCP/IP and IPX, and media such as fiber-optic cabling.
Posted by
Sunflower
at
7/07/2009 03:50:00 PM
0
comments
![]()
Labels: Architecture, Network, Technical Tip
|
| Subscribe by Email |
|
Quick Tip: URLs - Uniform Resource Locator
URLs, or Uniform Resource Locators, are the method by which documents or data are addressed in the World Wide Web. The URL contains the following information:
- the protocol.
- the DNS name of the machine on which the page is located.
- the local name uniquely indicating the specific page.
- the location of the resource in the directory structure of the server.
To make a piece of text clickable, the page writer must provide two items of information : the clickable text to be displayed and the URL of the page to go to if the text is selected. Once the text is selected, the browser looks up the host name using DNS. Now armed with the host's IP address, the browser establish TCP connection to host. Over that connection, it sends the file name using the specified protocol.
The URL scheme is open to have protocols other than HTTP also. In short, URL's have been designed to not only allow users to navigate the Web, but to deal with FTP, news, Gopher, email, and telnet as well, making all the specialized user interface programs for those other services unnecessary, and thus integrating nearly all Internet access into a single program, the Web Browser.
The growing use of the Web has turned up an weakness in URL scheme. A URL points to one specific host. For pages that are heavily referenced, it is desirable to have multiple copies far apart, to reduce network traffic. The advent of systems such as Akami are meant to meet that need, distributing content over multiple servers on a global level.
Posted by
Sunflower
at
7/07/2009 02:52:00 PM
0
comments
![]()
Labels: DNS, IP address, Protocol, Uniform Resource Locator, URL, Web Applications, Web page, World wide web, WWW
|
| Subscribe by Email |
|
Wednesday, July 1, 2009
WWW - The Server Side
For all the incoming connectionts from different clients, every website is associated with a server process listening to TCP port 80. The client sends a request after the connection is made and the server sends the reply and then the connection is released. The protocol that is responsible for requests and replies is called HTTP.
The steps that occur between the user clicking and a page being displayed are:
- The browser determines the URL.
- The browser asks DNS for IP address.
- DNS replies.
- Browser makes a TCP connection to the port.
- It then sendsthe GET command.
- The server sends the file.
- The TCP connection is released.
- The browser displays the text of the file.
- The browser fetchesand displays all images of the file.
Not all servers speak HTTP, Old servers use FTP, Gopher or other protocols. Given the number of different protocols, it was thought impractical to make browser understand different protocols. However, since there is a need to make information available (where the server talks in protocols other than HTTP), a solution was required. This solution is something called a proxy server. A proxy server takes a HTTP request from the browser and translates these requests into the FTP/Gopher/other protocols. The proxy server is a separate logical server.
A proxy server also serves to provide an important function called caching. Through caching, a proxy server keeps a local copy of the pages that pass through it. If a user requests for a page, if the page is present on the cache of the proxy server, it serves the page to the user. this way it serves to reduce load on final server.
Posted by
Sunflower
at
7/01/2009 05:32:00 PM
0
comments
![]()
Labels: Browsers, Connection, FTP, Gopher, HTTP, IP address, Protocol, Server, TCP, World wide web, WWW
|
| Subscribe by Email |
|
Introduction: WWW - The Client Side
The Internet / World Wide Web consists of pages and each page contains links or pointers to other pages. Users follow the link by clicking on them. This process can be repeated indefinitely, possibly traversing hundreds of linked pages. Pages that point to other pages are said to use "hypertext".
Pages are viewed with a program called a browser. When a page is requested, the browser fetches, interprets the text and formats the commands that it contains and displays the page. Strings of text that are links to other pages are called hyperlinks.
Most browsers have numerous buttons and features to navigate the Web. In addition to having ordinary text and hypertext, web pages also contain icons, line drawings, maps and photographs. Some pages also consist of audio tracks, video clips, or both. When hypertext pages are combined with other media, the result is called hypermedia. Many Web pages consists of large images which take a long time to load.
Some browsers deal with slow loading of images by first fetching and displaying the text, then getting the images. Some Web pages contain forms that request the user to enter information. Some browsers use the local disk to cache pages that they have fetched. A check is made before a page is fetched to see if it is in the local cache. If so, check if it is up to date. If so,there is no need to load the page again.
To host a web browser, a machine must be directly connected to Internet or have a SLIP or PPP connection to a router or other machine that is directly on Internet.
Posted by
Sunflower
at
7/01/2009 04:55:00 PM
0
comments
![]()
Labels: Browsers, Client, Hypermedia, Hypertext, Internet, Page, Web Applications, World wide web, WWW
|
| Subscribe by Email |
|
Quick Introduction to the World Wide Web (WWW) / Internet
The World Wide Web is an architectural framework for accessing linked documents spread out over thousands of machines all over the Internet. The World Wide Web began as a networked information project at CERN, where Tim Berners-Lee, now Director of the World Wide Web Consortium [W3C], developed a vision of the project.
The Web has a body of software, and a set of protocols and conventions. Through the use of hypertext and multimedia techniques, the web is easy for anyone to roam, browse, and contribute to.
World Wide Web can also be defined as system of Internet servers that support specially formatted documents. The documents are formatted in a markup language called HTML (HyperText Markup Language) that supports links to other documents, as well as graphics, audio, and video files. You can jump from one document to another simply by clicking on hot spots. Not all Internet servers are part of the World Wide Web. Web is basically a client-server system. Web pages are written in HTML and java.
Posted by
Sunflower
at
7/01/2009 04:34:00 PM
0
comments
![]()
Labels: CERN, Client, HTML, Internet, Server, World wide web, WWW
|
| Subscribe by Email |
|