Tuesday, October 1, 2013
How can firewalls secure a network?
Posted by
Sunflower
at
10/01/2013 07:30:00 AM
0
comments
![]()
Labels: Application layer, attacks, Communication, Control, Data, Firewalls, Hardware, Layers, Network, Network layer, Networking, Packets, Protocols, Secure, Security, Software, System, Threats, traffic
|
| Subscribe by Email |
|
Saturday, August 31, 2013
What is the difference between leaky bucket algorithm and token bucket algorithm?
Posted by
Sunflower
at
8/31/2013 04:10:00 PM
0
comments
![]()
Labels: Algorithms, Bandwidth, Bucket, Data, Events, Inter-network, Interfaces, Layers, Leaky bucket algorithm, Network, Network layer, Networking, Packets, Processes, Token, Token bucket algorithm, transmission, Virtual
|
| Subscribe by Email |
|
Wednesday, July 17, 2013
What are network layer design issues?
- Services
provided to the layer 4 i.e., the transport layer.
- Implementation
of the services that are connection oriented.
- Store
– and - forward packet switching
- Implementation
of the services that are not connection oriented.
- Comparison
of the data-gram sub-nets and the virtual circuits.
- They
should be independent of the router technology.
- Shielding
from the type, number and topology of the routers must be provided to the
transport layer.
- The
network addresses that are provided to the transport layer must exhibit a
uniform numbering plan irrespective of whether it’s a LAN or a WAN.
Posted by
Sunflower
at
7/17/2013 05:30:00 PM
0
comments
![]()
Labels: Communication, Connection, Data, Datagram, Design, Hosts, Issues, Layers, Model, Network, Network layer, OSI, Packets, Processes, Routes, Routing, subnet, Tasks, Transport layer, Virtual Circuits
|
| Subscribe by Email |
|
Tuesday, July 16, 2013
What are the characteristics of network layer?
Posted by
Sunflower
at
7/16/2013 05:26:00 PM
0
comments
![]()
Labels: Address, Communication, Decapsulation, Destination, Encapsulation, Frames, Functions, Host, Layers, Message, Network layer, Networking, OSI, Packets, Process, Protocols, Routers, Routing, Source
|
| Subscribe by Email |
|
Wednesday, July 10, 2013
Explain the concept of piggybacking?
Posted by
Sunflower
at
7/10/2013 01:30:00 PM
0
comments
![]()
Labels: Acknowledge, Data, Frames, Internet, Layers, Network layer, Operating System, OSI, Packets, Piggybacking, Protocols, Receiver, Sender, Signals, Technique, Transfer, transmission, Transmit, Uses
|
| Subscribe by Email |
|
Thursday, January 5, 2012
What are different aspects of network testing?
Network is interconnected collection of hardware components and computers interconnected by communication channels which shares data and resources. Computers are said to be interconnected if they are capable of sharing data and information. These computers are said to be autonomous since no computer can start, stop and control the other computer.
NEED OF NETWORK
- Network is needed because through network we can share resource which means we can make all programs, data and peripherals available to anyone on the network irrespective of the physical location of the resources and user.
- It provides reliability i.e.a file can have copies on two or three different machines, so if one of them is not available ,the other copies can be used.
- It also affects the cost factor which means personal computer have better price/performance ratio then the micro computers.
- Using a network, it is possible for managers, working far apart, to prepare financial report for the company.
- The changes at one end can be noticed at another and hence it speeds up the co-operation among them.
Network has some disadvantages also.
- Network makes systems more sophisticated and complex to run.
- This can add to costs and you may need a specialist staff to run the network. - If software and files are held centrally, it may be impossible to carry out any work if the central server fails.
- If networks are badly managed services can become unusable and productivity fails.
- File security is more important especially if connected to WAN e.g. protection from viruses.
Network testing is done by various types of tools. These tools help us to test switches, routers, servers and other networks. Network testing aims at determining the strength of the integrity of the network.
- Network testing methodology aims at testing the networking equipments and live networks.
- Network testing requires the network to adhere to the standards of networking. - It doesn’t matter what the software testers test the network for inter- operability, scalability, performance or protocol conformance, they can always rely only network testing for in depth and un biased testing of the network.
Speed testing is another aspect of network testing.
- Speed test can be used to verify if the internet service provider is delivering the connection speed that they promised or not.
- These days network equipment face validation challenges.
- There is a dire need of improving the quality and the performance of the core product.
- While the network complexity is constantly increasing, the process of network testing is increasingly becoming more intricate and time consuming.
There are certain problems that arise while performing the network test. They have been listed below:
- The complex combination of software, firmware and hardware components makes it very difficult to test a particular device as a single integrated system. Such cases often require manual intervention.
- The streamlining of remote manufacturing processes not only makes the whole testing process more complicated but it also makes it difficult to meet the market requirements on time.
- Performing network testing across a wide variety of scripts, testing equipments and network protocols requires complex configuration processes and long set up.
Whether the network to be tested is WAN (wide area network), LAN (local area network), VPN (virtual private network, data center products or other networking devices, network testing over comes their validation challenges and at the same time it increases test automation coverage and provides massive reduction in overhead testing costs and time consumption.
These days automated network testing set up is available. It significantly reduces the test duration, coverage and optimized test operations. Such set ups offer complete automation and configuration of the test prior to testing. The created test cases confirm to standards and provide maximum flexibility and re-usability.
Posted by
Sunflower
at
1/05/2012 12:24:00 PM
0
comments
![]()
Labels: Advantages, Automated, Components, computers, Data, files, Hardware, Need, Network, Network layer, Network testing, Operations, Optimize, peripherals, program, Resources, Software testing, Tests
|
| Subscribe by Email |
|
Friday, July 31, 2009
Quick Tech Tip: Overview Of The Network Layer
The network layer provides services to the transport layer through virtual circuits or datagrams. In both cases, its main job is routing packets from the source to the destination. In virtual circuit subnets, a routing decision is made when the virtual circuit is set up. In datagram subnets, it is made on every packet.
Many routing algorithms are used in computer networks. Static algorithms include shortest path routing, flooding, and flow-based routing. Dynamic algorithms include distance vector routing and link state routing. Most actual networks use one of these. Other important routing techniques are hierarchical routing, routing for mobile hosts, broadcast routing, and multicast routing.
Subnets can become congested, increasing the delay and lowering the throughput for packets. Techniques include traffic shaping, flow specifications, and bandwidth reservation. If congestion does occur, it must be dealt with. Choke packets can be sent back, load can be shed, and other methods applied.
Networks differ in various ways, so when multiple networks are connected together problems can occur. Sometimes problems can be finessed by tunneling a packet through a hostile network, but if the source and the destination networks are different, this approach fails. Fragmentation may be called for if different networks are having different maximum sizes.
The Internet has a rich variety of protocols related to the network layer. These include the data protocol, IP, but also the control protocols ICMP, ARP, and RARP, and the routing protocols OSPF and BGP. The Internet is rapidly running out of IP addresses, so a new version of IP, IPv6, has been developed.
Unlike the datagram-based Internet, ATM networks use virtual circuits inside. There must be a set up before data can be transferred and torn down after transmission is completed. Quality of service and congestion control are major issues with ATM networks.
Posted by
Sunflower
at
7/31/2009 10:43:00 AM
0
comments
![]()
Labels: Concatenated Virtual Circuits, Congestion, Datagrams, Network layer, Networks, Packets, Technical Tip
|
| Subscribe by Email |
|
Friday, July 24, 2009
Introduction to Firewalls
A firewall is a hardware or software system that prevents unauthorized access to or from a network. They can be implemented in both hardware and software, or a combination of both. Firewalls are frequently used to prevent unauthorized Internet users from accessing private networks connected to the Internet. All data entering or leaving the Intranet pass through the firewall, which examines each packet and blocks those that do not meet the specified security criteria.
Firewalls can greatly enhance the security of a host or a network. They can be used to do one or more of the following things:
* To protect and insulate the applications, services and machines of your internal network from unwanted traffic coming in from the public Internet.
* To limit or disable access from hosts of the internal network to services of the public Internet.
* To support network address translation (NAT), which allows your internal network to use private IP addresses and share a single connection to the public Internet (either with a single IP address or by a shared pool of automatically assigned public addresses).
FIREWALL CONCEPTS
There are two basic ways to create firewall rulesets: “inclusive” or “exclusive”. An exclusive firewall allows all traffic through except for the traffic matching the ruleset. An inclusive firewall offers much better control of the outgoing traffic, making it a better choice for systems that offer services to the public Internet. It also controls the type of traffic originating from the public Internet that can gain access to your private network. All traffic that does not match the rules, is blocked and logged by design.
Inclusive firewalls are generally safer than exclusive firewalls because they significantly reduce the risk of allowing unwanted traffic to pass through them.
HOW FIREWALLS WORK ?
A firewall, working closely with a router program, examines each network packet to determine whether to forward it toward its destination. A firewall also includes or works with a proxy server that makes network requests on behalf of workstation users. A firewall is often installed in a specially designated computer separate from the rest of the network so that no incoming request can get directly at private network resources.
Firewalls use one or more of three methods to control traffic flowing in and out of the network:
* Packet filtering - Packets are analyzed against a set of filters. Packets that make it through the filters are sent to the requesting system and all others are discarded.
* Proxy service - Information from the Internet is retrieved by the firewall and then sent to the requesting system and vice versa.
* Stateful inspection - It compares certain key parts of the packet to a database of trusted information. Information traveling from inside the firewall to the outside is monitored for specific defining characteristics, then incoming information is compared to these characteristics. If the comparison yields a reasonable match, the information is allowed through. Otherwise it is discarded.
Posted by
Sunflower
at
7/24/2009 10:34:00 AM
0
comments
![]()
Labels: Concepts, Firewalls, How does firewall work, introduction, Network layer, w
|
| Subscribe by Email |
|
Introduction to Packet Fragmentation
Each network imposes some maximum size on its packets. The network designers are not free to choose any maximum packet size they wish as there are various factors like hardware, operating system, protocols, compliance with some (inter)national standard, desire to reduce error induced transmissions to some level and desire to prevent one packet from occupying the channel too long.
Packets larger than the allowable MTU (Maximum Transmission Unit) must be divided into multiple smaller packets, or fragments, to enable them to traverse the network.
If a packet that is about to be sent (for eg : over an Ethernet link) is bigger than that, the router which is about to send the packet over that link will fragment the packet i.e. the router will split the packet up into smaller messages (known as fragments) that are each small enough to be transmitted over the link. When the fragments arrive at their destination (the computer to which they are being sent), that computer can reassemble the fragments to recover the original message - assuming none of the messages are lost in transit.
How can be fragmentation avoided ?
If the option of "don't fragment" is set ON in IP version 4, and the router wants to send the packet over a link for which the packet is too large, the router will not send the packet at all. Instead, the router will send a message back to the sender of the packet that was too large. The sending computer can then respond to this by sending out smaller packets. This is known as "path MTU discovery".
Strategies for recombining fragments :
- Transparent Fragmentation : When an oversized packet arrives at gateway, the gateway breaks it into smaller fragments, each fragment is addressed to same exit gateway, where pieces are recombined. In this way passage through the small packet network has been made transparent.
Benefits : It maximizes bandwidth on higher links and deterministic fragmentation unlikely.
Drawbacks : Packets may be reassembled/fragmented, gateways more complex, performance gains bounded because the max TU will be the MTU of the first hop. Plus, the IP layer at the destination may still have to perform reassembly if the last link had a smaller MTU than the first link. Only use on links with unusually small MTUs. 
- Non transparent Fragmentation : This strategy includes refraining the recombining of fragmented packets at intermediate gateway. Once a packet is fragmented, each fragment is treated as an original packet. All fragments are passed through the exit gateway. Recombination exists only at destination host.
Benefits : Multiple exit gateways can now be used and higher performance can be achieved.
Drawbacks : Overhead increases. Also, it requires every host to be able to do reassembly.
Posted by
Sunflower
at
7/24/2009 09:35:00 AM
0
comments
![]()
Labels: Fragmentation, Network layer, Networks, Non Transparent fragmentation, Packet fragmentation, Transparent fragmentation
|
| Subscribe by Email |
|
Thursday, July 16, 2009
Quick Tech Tip: Concatenated Virtual Circuits
Two styles of internetworking are common:
* a connection-oriented concatenation of virtual circuit subnets,
* a datagram internet style.
In the concatenated virtual circuit model, a connection to a host in a distant network is set up in a way similar to the way connections are normally established. The virtual circuit consists of concatenated virtual circuits between the routers or gateways along the way from the source node to the destination node. Each gateway maintains tables telling which virtual circuits pass through it, where they are to be routed, and what the new virtual circuit number is. This process continues until the destination host has been reached.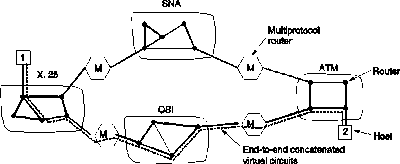
Once data packets begin flowing along the path, each gateway relays incoming packets, converting between packet formats and virtual circuit numbers as needed. Clearly, all data packets must traverse the same sequence of gateways , and thus arrive in order.
This scheme works best when all the networks have roughly the same properties.
Concatenated virtual circuits are also common in the transport layer. In particular, it is possible to build a bit pipe using OSI, which terminates in a gateway, and have a TCP connection go from the gateway to the next gateway. In this manner, an end-to-end virtual circuit can be built spanning different networks and protocols.
Posted by
Sunflower
at
7/16/2009 12:16:00 PM
0
comments
![]()
Labels: Concatenated Virtual Circuits, Gateways, Internetworking, Network layer, Packets, Routers
|
| Subscribe by Email |
|